Cybersecurity services for an
international outsourcing firm
In this case study, we highlight our collaboration with an international outsourcing firm, showcasing our team, the process we followed, and the successful results achieved through our dedicated approach to cybersecurity consulting.
Services Used
Cybersecurity consulting
Industry
Professional services
[ ABOUT THE CLIENT ]
Customer
Based in Europe, this international outsourcing company has a team of 800 dedicated employees spread across five key offices worldwide. They specialize in IT outsourcing, working with clients in various industries to deliver customized solutions that meet specific needs. However, they faced challenges in cybersecurity. To address this, they sought QatSol’s expertise to enhance their security measures and better protect their clients’ sensitive information.
[ identify, mitigate and prevent ]
Challenge
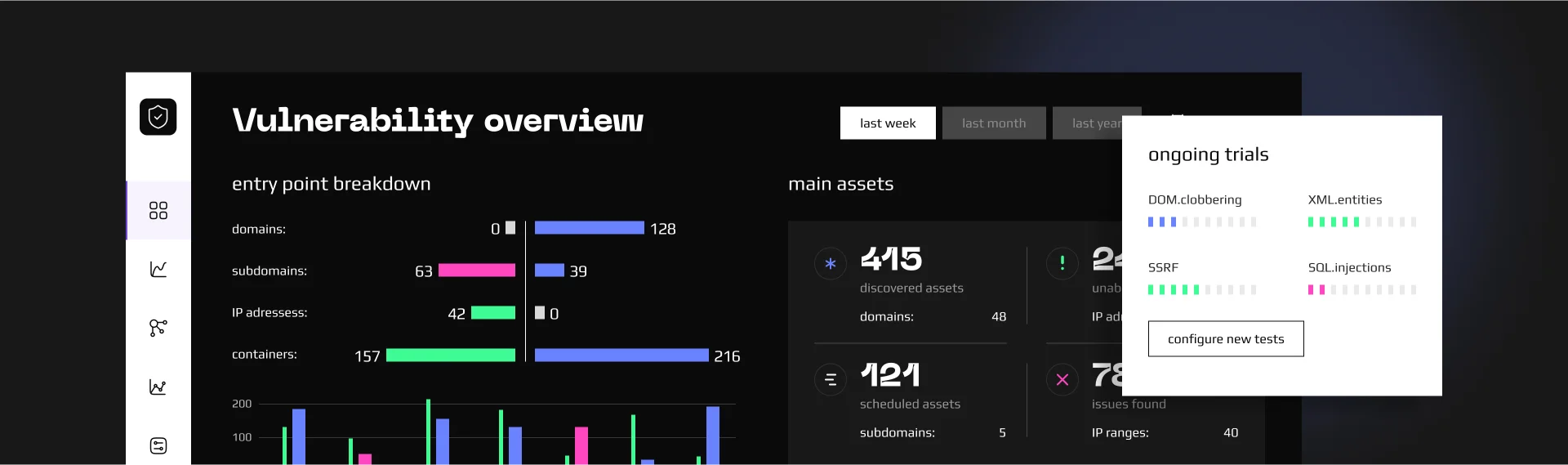
QatSol was tasked with conducting an extensive security assessment for the client, covering both their network infrastructure and web applications. Additionally, the engagement included email phishing campaigns aimed at enhancing employee awareness and uncovering potential social engineering vulnerabilities.
Remediation Period:
- The client dedicated approximately 1.5 months to address identified vulnerabilities and misconfigurations.
Quick Re-Testing:
- QatSol initiated a re-testing campaign to ensure that fixes were correctly implemented.
- Identified any remaining issues and confirmed that critical vulnerabilities were mitigated.
Risk Management Acceptance:
- Some medium-severity issues were accepted by the client’s risk management policy.
- Emphasized the importance of balancing security with operational needs.
[ Team ]
It took 10 QatSolers to implement a complete security assessment.
1
Project Manager
Ensured seamless communication and milestone tracking
2
Cybersecurity Consultants
Conducted the security assessment and provided remediation guidance
1
System Analysts
Analyzed the client’s existing security measures and identified areas for improvement
3
Penetration Testers
Executed network and web application testing using industry-standard tools
1
Social Engineering Specialist
Designed and executed phishing campaigns
1
QA Engineer
Ensured the accuracy and reliability of the testing results
1
Report Specialist
Compiled detailed reports, translating technical findings into actionable insights for the client
[WE HIRE THE BEST TALENT]
Industry-leading tech stack
With over 500 developers, expert engineers, and cutting-edge tools, QatSol is fully equipped to help you design scalable architectures, implement robust development pipelines, create custom automation solutions, and achieve your technology goals.
[ in-depth assessment ]
Solution
QatSol executed a multi-faceted security testing engagement, leveraging a combination of advanced penetration testing techniques and social engineering strategies. Our approach was designed to provide a thorough evaluation of the client’s security posture, uncover critical vulnerabilities, and recommend actionable remediation steps.
The penetration testing and social engineering engagement provided invaluable insights into the client’s security posture, uncovering critical vulnerabilities and potential risks. The successful social engineering campaigns underscored the need for continuous user awareness and training.
The remediation process and subsequent re-testing rounds demonstrated the client’s commitment to enhancing their security measures. Ongoing collaboration with the client’s risk management policies emphasized a pragmatic approach to addressing security issues while maintaining operational efficiency.
[ HOW WE DEVELOP ]
Process

01
Discovery and Planning
We started by discussing closely with the client to understand their specific needs and security concerns. Using their insights, we set clear project goals and developed a solid plan aligned with their vision and objectives.
02
Technology Selection
We selected a range of advanced tools and technologies, including the Metasploit Framework, custom spear phishing scripts, and various logging and monitoring tools. These choices enabled us to conduct thorough and effective security assessments.
03
Security Assessment
We employed a Gray Box testing model to assess the client’s security from both external and internal perspectives:
- Network Testing: We evaluated both external and internal networks, focusing on public-facing services, internal configurations, and Active Directory security.
- Web Application Testing: We assessed multiple web applications using OWASP Top 10 guidelines to identify common vulnerabilities such as XSS, SQL injection, and SSRF.
- Social Engineering: We conducted email phishing campaigns targeting 100 employees and spear phishing attacks on 10 management team members to test awareness and respons
04
Reporting & Re-Testing
Upon completing the initial testing, we provided comprehensive documentation including detailed reports, executive summaries and others. Following a 1.5-month remediation period, we conducted a re-testing campaign to ensure that fixes were correctly implemented and confirmed that critical vulnerabilities were mitigated.
[ a comprehensive security service ]
Features
Network Testing
- External Network Assessment:
- Evaluated the security of public-facing services.
- Identified services with default or weak credentials.
- Discovered outdated and vulnerable services.
- Internal Network Assessment:
- Analyzed internal network configurations and security controls.
- Detected potential lateral movement and privilege escalation paths.
- Active Directory Assessment:
- Reviewed Active Directory security configurations.
- Identified misconfigurations and potential attack vectors.
Web Application Testing
- Assessed multiple public-facing web applications
- Utilized OWASP Top 10 guidelines to identify common vulnerabilities
- Detected issues such as XSS, SQL injection, and SSRF
Social Engineering
- Email Phishing Campaign:
- Targeted 100 employees with simulated phishing emails to test awareness and response.
- Spear Phishing Campaign:
- Conducted targeted spear phishing attacks on 10 management team members to assess their susceptibility to personalized attacks.
Reporting and Collaboration
- Full Detailed Report:
- Comprehensive documentation of identified vulnerabilities, exploitation steps, and remediation recommendations.
- Executive Summary Document:
- High-level overview for non-technical stakeholders.
- Raw Export Results:
- Provided tools’ raw outputs for transparency and additional insights.
- Client Collaboration:
- Presented findings with detailed explanations.
- Facilitated discussions on the impact and remediation of identified issues.
- Maintained open communication throughout the engagement to ensure effective collaboration.
[ value-driven ]
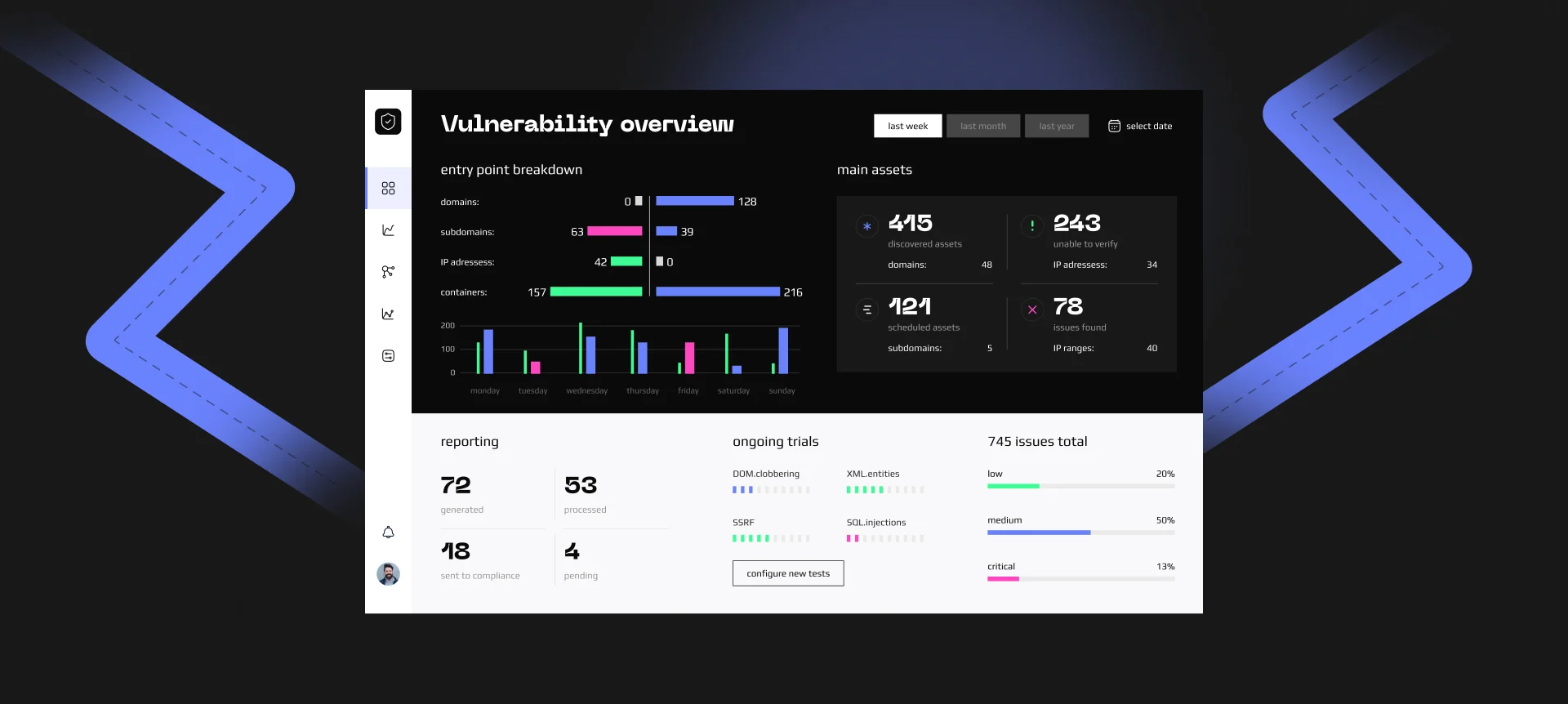
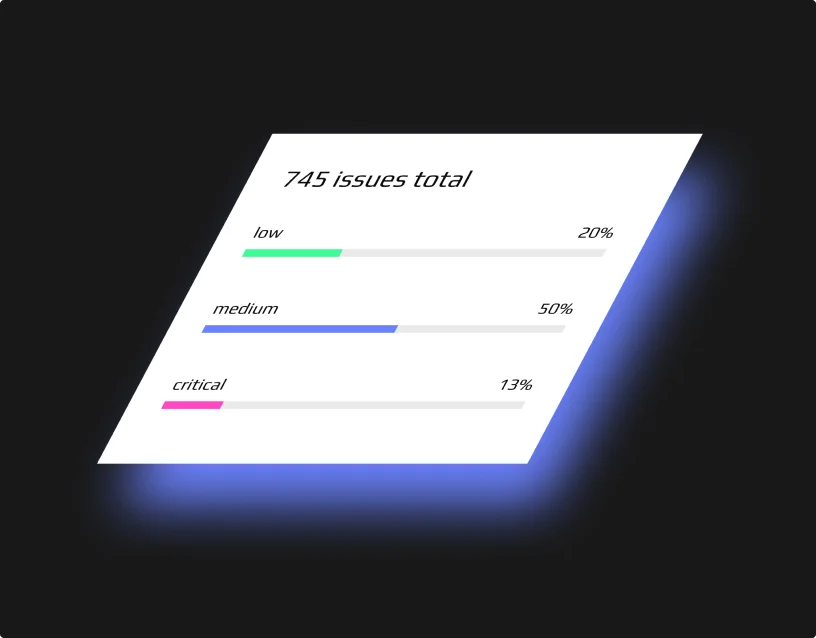
Results
Our comprehensive security assessment and penetration testing uncovered critical vulnerabilities across the client’s network infrastructure and web applications.
Identifying and mitigating security issues.
We identified and mitigated over 70 security issues, including vulnerabilities in public-facing services and internal network configurations.
Ensuring employee thread readiness.
Our email phishing campaigns targeted 50+ employees and seven management team members, raising awareness and improving response readiness.
Delivery of a comprehensive thread prevention roadmap.
Following our recommendations, the client implemented security enhancements that reduced potential attack vectors by 20% and significantly improved their overall security posture.
Direct collaboration with a risk unit helped us iterate quickly.
Our collaborative approach with the client’s risk management team ensured operational efficiency was maintained while effectively prioritizing cybersecurity measures.
[ TECH STACK ]
Technologies & tools
Ready to execute your product vision?